$34 USB嗅探器教程:使用Wireshark捕获鼠标移动和键盘击键
USB嗅探器教程:使用Wireshark捕获鼠标移动和键盘按键输入
在这个项目中,我们探讨了如何使用USB嗅探器设备来监控和分析计算机与常见输入设备(如鼠标和键盘)之间的USB通信。通过将USB嗅探器放置在USB设备和计算机之间的线路中,可以实时捕获和分析通过的所有USB数据包,使用Wireshark进行分析。

本教程演示了如何在USB协议级别观察鼠标移动、按钮点击甚至键盘击键(包括密码)。该项目旨在用于教育目的,以理解USB人机接口设备(HID)如何在内部工作,以及为什么物理安全与软件安全同样重要。

什么是USB嗅探器?
USB sniffers 是一种硬件设备,位于 USB 外设(如鼠标或键盘)与主机计算机之间。它透明地传递数据,使设备正常工作,同时通过单独的监控接口捕获并展示 USB 数据包。
在这个项目中,USB嗅探器充当了一个透传设备:
- USB鼠标或键盘连接到嗅探器
- 嗅探器连接到计算机。
- 来自嗅探器的独立USB连接接到运行Wireshark的监控计算机。
所有在设备与计算机之间传输的 USB 流量都可以被捕获和解码,而不会影响正常操作 :contentReference[oaicite:0]{index=0}。

主要使用的组件
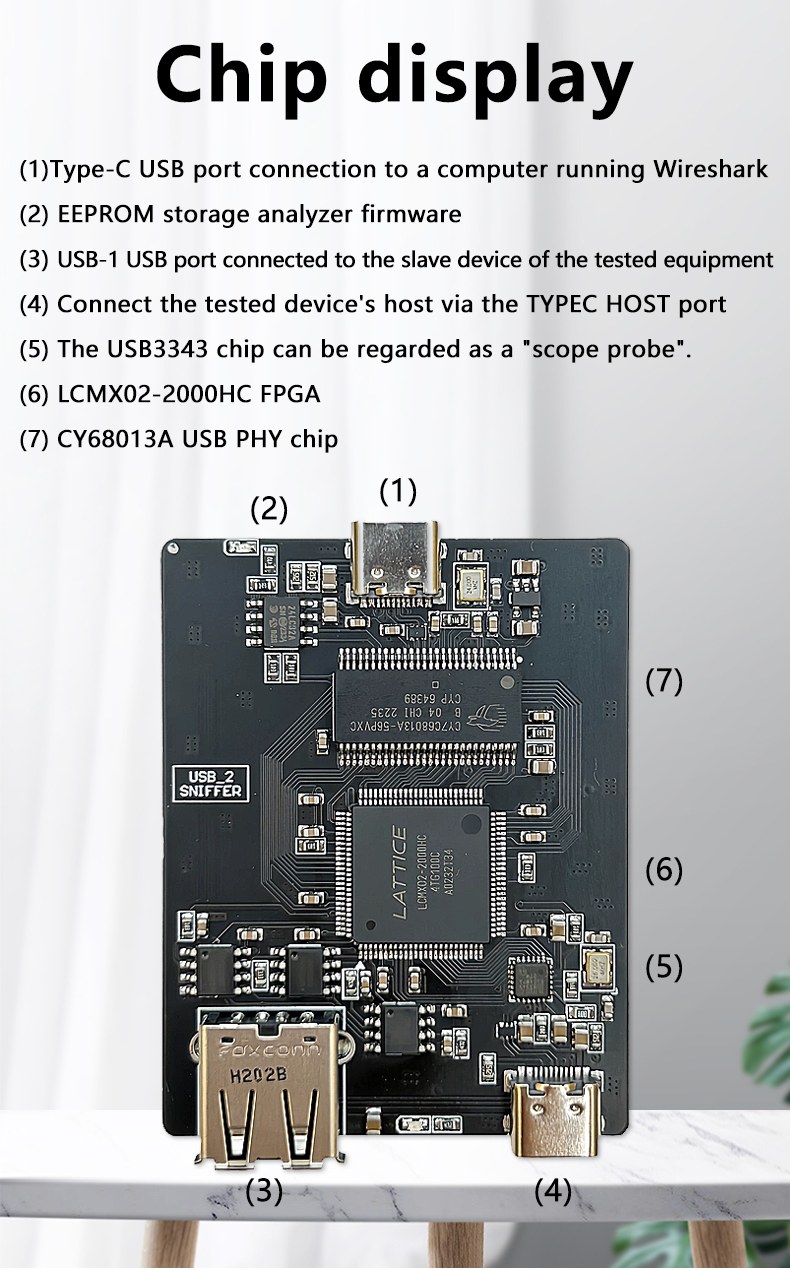
USB嗅探器硬件
本项目中使用的USB嗅探器基于Alex Tarasov创建的FPGA设计。完整设计包括固件、PCB文件和软件工具。这里使用的商业单元预装了固件,因此在使用前无需刷写或配置。
在内部,嗅探器连接到USB差分数据线,并将数据包镜像到一个独立的USB接口,Wireshark可以监控该接口。
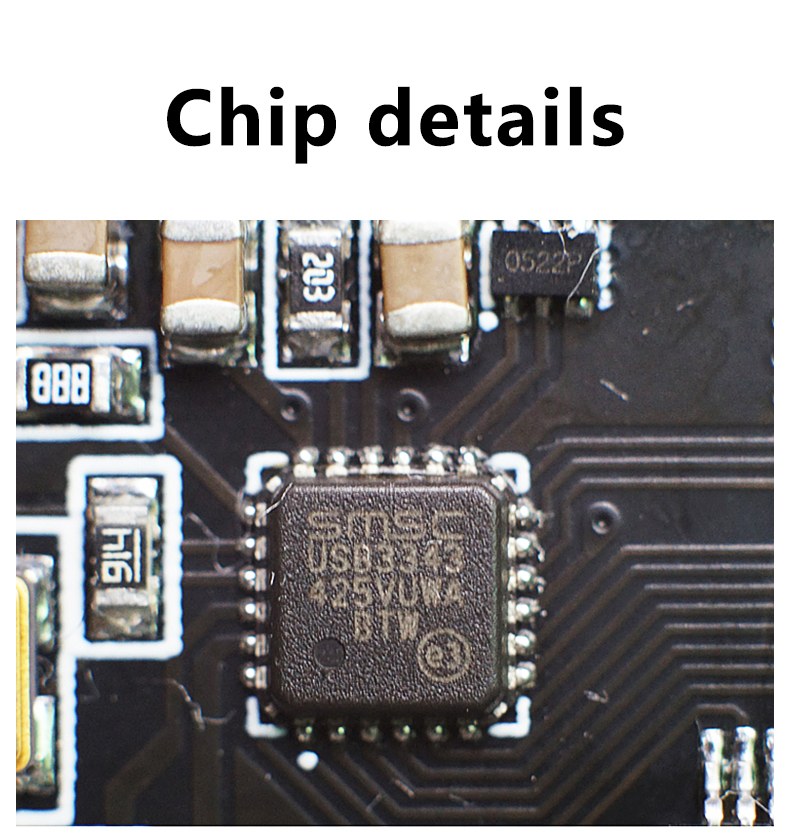
鼠标和键盘(USB HID 设备)
鼠标和键盘都是USB人机接口设备(HID)。这些设备定期向主机计算机发送报告,描述它们的状态:
- 鼠标:按钮状态,X 方向移动,Y 方向移动
- 键盘:修饰键和按键扫描码
这些报告以明文、未加密的形式通过USB传输,这就是它们可以被嗅探器捕获的原因。
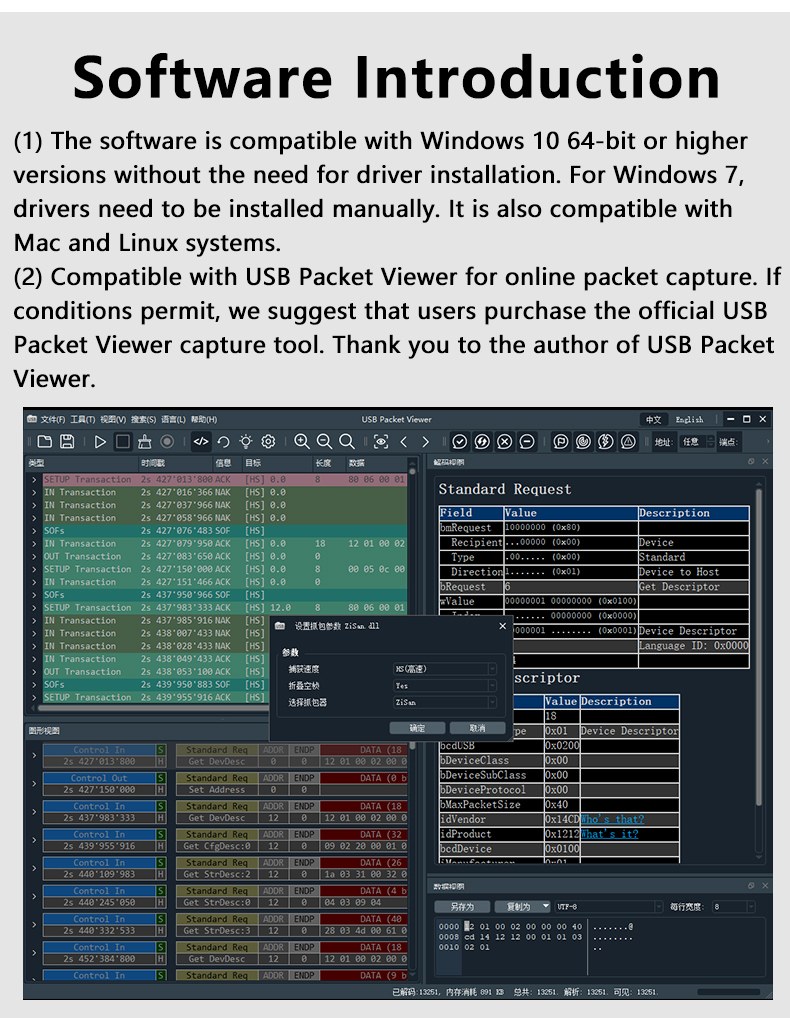
带有Wireshark的计算机
Wireshark 用于捕获和分析 USB 数据包。在 Windows 上,USB 捕获需要额外的组件以启用对驱动程序级别 USB 流量的访问。
接线和连接
USB嗅探器连接在USB设备和计算机之间的线路中。
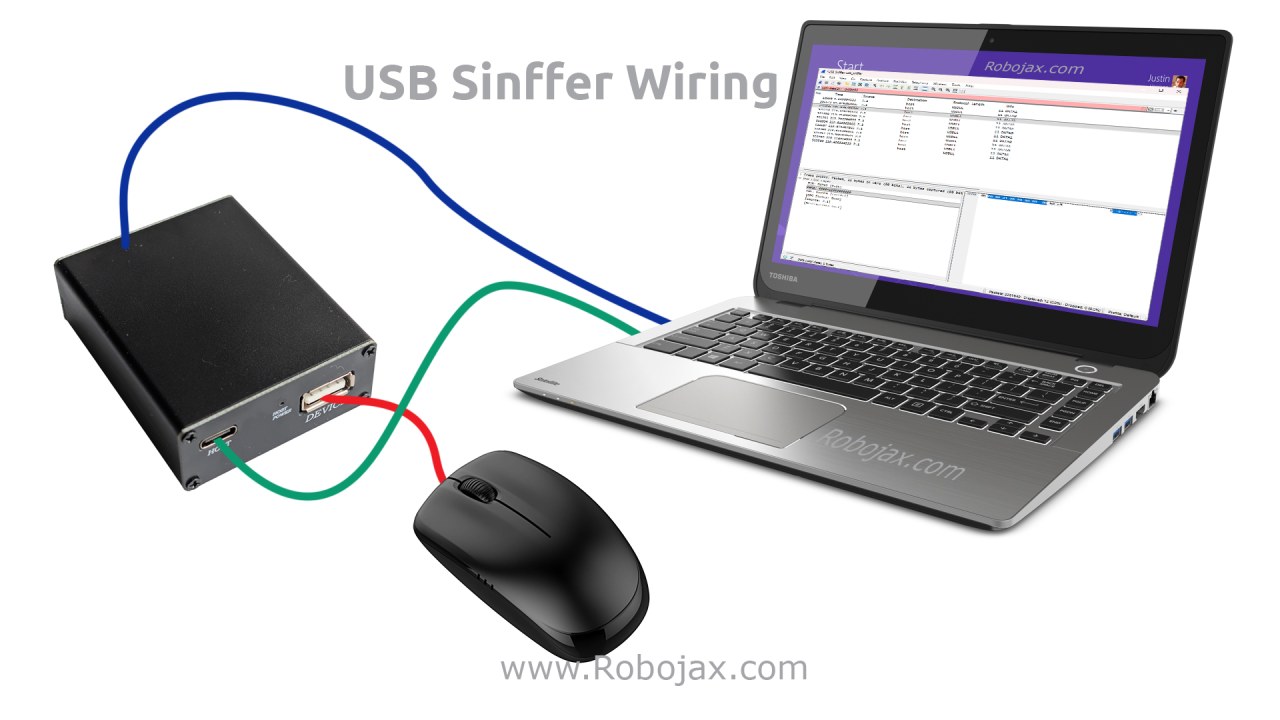


- 将鼠标或键盘连接到嗅探器的USB输入端口。
- 将嗅探器的USB输出端口连接到电脑上。
- 将嗅探器的监控USB端口连接到运行Wireshark的同一台或另一台计算机。
USB设备在其流量被镜像到监控端口时仍然正常工作。
安装所需软件
Wireshark 安装
Wireshark 必须安装在监控计算机上。在 Windows 上安装时,必须启用 USB 捕获支持组件。如果没有这个驱动程序,则无法捕获 USB 流量。
安装后,Wireshark将会将USB捕获接口与网络接口并列展示。
USB嗅探器驱动程序(Windows)
在Windows上需要一个小的辅助可执行文件,以便Wireshark能够访问硬件的USB嗅探数据。该可执行文件必须放置在系统路径中(例如,直接放在C:驱动器下),以便Wireshark可以与嗅探器进行通信。
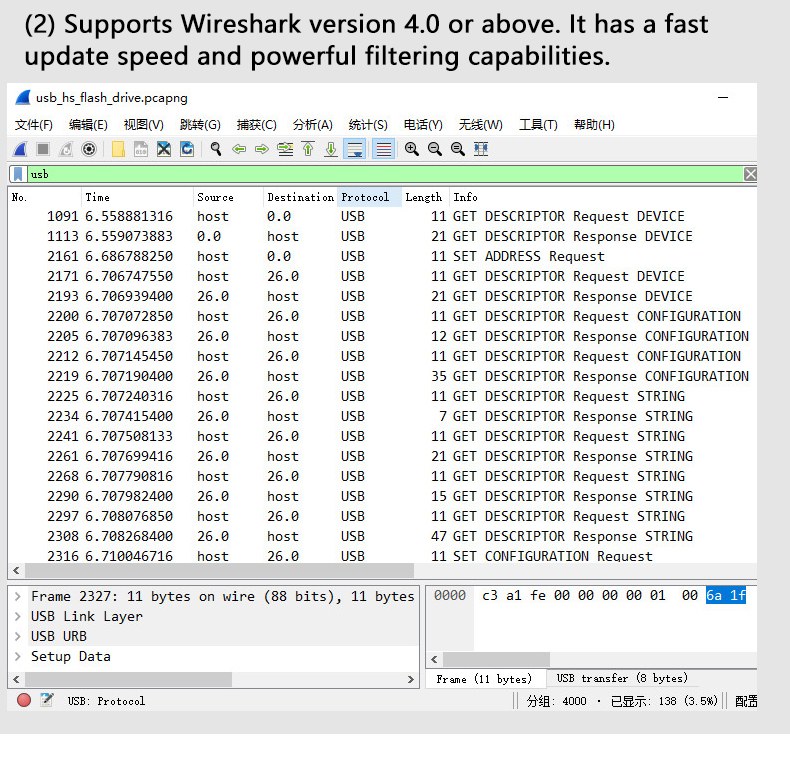
在Wireshark中捕获USB数据
启动Wireshark后,选择USB嗅探器接口并开始捕获。最初,可能会出现大量无关的USB流量。

应用USB过滤器
为了仅关注相关的USB数据,应用了显示过滤器:
usbll此过滤器仅显示USB链路层数据包,其中包含设备与主机之间交换的原始USB事务。
由于USB产生的数据量非常大,因此需要进一步筛选。
按包 ID (PID) 过滤
鼠标和键盘数据包可以通过特定的包 ID (PID) 进行识别。在该项目中,观察到的相关 PID 有:
0xC30x4B
可以在Wireshark中使用以下方式进行过滤:
usbll.pid == 0xC3 || usbll.pid == 0x4B此过滤器隔离来自鼠标或键盘的HID报告数据包。
理解鼠标数据
当鼠标移动或点击时,HID 报告会连续发送。每个报告包含几个字节:
- 报告编号
- 按钮状态(左,右,中)
- X轴运动
- Y轴移动
通过观察Wireshark中变化的字节值,可以推断出鼠标的移动方向和速度。即使不点击,仅移动也会产生可见的USB活动。
理解键盘数据
键盘数据以HID报告的形式发送,包含扫描码而不是ASCII值。每个按键对应一个特定的HID使用ID。
例如:
0x04→ 字母A0x05→ 字母B0x0EK字母
大写和小写字母由修饰键确定,例如 Shift,这些键在报告中以单独的字节出现。
功能键如 F12 也会生成独特的扫描码,这些码可以直接在捕获的数据包中观察到。
安全隐患
该项目清楚地表明,USB HID 流量并未加密。如果将恶意设备物理放置在键盘和计算机之间,它可以捕获每一个按键,包括用户名和密码。
这就是为什么在敏感环境中,USB安全、可信硬件和物理访问控制至关重要。
演示摘要
在这个演示中,以下内容被成功捕获和解码:
- 鼠标移动和按钮活动
- 单个键盘按键的按压
- 功能键和修饰键
- 在键盘上输入的完整单词
USB嗅探器以透明的方式运行,导致在没有物理检查的情况下难以被检测。
结论
这个USB嗅探器项目提供了一个强大的动手演示,展示了USB通信在最低层面的工作原理。通过将专用的嗅探硬件与Wireshark结合,可以准确地看到输入设备是如何与计算机通信的。
该项目非常适合学习USB协议、HID报告结构以及现实世界的安全考虑。虽然使用鼠标和键盘进行演示,但这些原理同样适用于许多其他USB设备。
软件下载
Windows辅助应用程序usb_sniffer_win.exe用于使用Wireshark捕获USB数据的所需内容可在本文下方下载。
|||您可能需要的东西
-
亚马逊从亚马逊购买USB嗅探器amzn.to
-
易趣从eBay购买USB嗅探器ebay.us
-
全球速卖通从AliExpress购买USB嗅探器。s.click.aliexpress.com
-
Banggood从Banggood购买USB嗅探器banggood.com
资源与参考
-
下载下载 Wiresharkwireshark.org
文件📁
用户手册
-
USB Sniffer 用户手册_英文
usb_sniffer_manual_english-1.pdf1.06 MB
其他文件
-
usb_sniffer_win.exe
usb_sniffer_win.zip0.29 MB